Shared Service
Definition:
A shared service, such as the Domain Name System (DNS), is utilized by multiple tenants (organizations) within the network.
Provisioning Shared Services in Cisco ACI
Options Based on Network Design:
Using a Common Tenant's VRF:
Services are hosted within the Virtual Routing and Forwarding (VRF) of a common tenant.
These services are made accessible to other tenants.
VRF Route Leaking:
Routes that provide access to shared services are shared (leaked) to the VRFs of the required tenants.
This method ensures that only necessary routes are exposed to specific tenants.
Common Tenant Objects Accessible by Other Tenants
Contracts:
Configured within the common tenant.
Can be associated with Endpoint Groups (EPGs) of other tenants to define communication policies.
VRF (Virtual Routing and Forwarding):
Commonly used to segregate and manage routing domains.
Facilitates the sharing of routing information between tenants as needed.
BD (Bridge Domain):
Commonly used to define Layer 2 segments.
Allows multiple tenants to connect to the same Layer 2 network infrastructure.
L3Out (Layer 3 Outside):
Used to connect the internal network to external networks.
Enables tenants to access external resources or the internet through shared Layer 3 connections.
VRF Route Leaking in ACI
For EPG 1 to be able to communicate with EPG 2, there are two things to consider.
Leak the subnets for EPG 1 and EPG 2 into each VRF for forwarding & allow the traffic with a contract for security.
The above objective will be achieved with the help of contract.
Scope of Contract
VRF (Default): traffic from EPGs is routed within VRF.
Application Profile : When two EPGs are in the same application profile in the same tenant.
Tenant Level : EPGs are in two different VRFs are in the same tenant.
Global : When EPGs are in different tenants.
Configuring VRF Route Leaking in Cisco ACI
1. Setting the Scope for Route Leaking
Options for Scope:
Global: Applies universally across the entire fabric.
Tenant: Limited to specific tenants.
Application Profile: Scoped to particular application profiles.
Requirement:
Determine and set the appropriate scope based on the network design and isolation requirements.
2. Subnet Configuration for Route Leaking
Provider Side:
Configuration Needed:
Subnets must be configured under the Endpoint Group (EPG) on the provider side.
This ensures that the provider can advertise the necessary routes for route leaking.
Consumer Side:
Configuration Flexibility:
There is no strict requirement to configure subnets under the EPG on the consumer side.
Allows for more flexible integration with consumer tenants.
3. Managing Contracts Between Tenants
Visibility of Contracts:
User Tenant Contracts:
Contracts within a user tenant are not visible to other user tenants by default.
Exporting Contracts:
From Provider to Consumer Tenant:
Contracts can be explicitly exported from the provider tenant to the consumer tenant.
Facilitates controlled sharing of policies and services.
Global Scope Contracts:
Common Tenant Usage:
If a contract with a global scope resides in the common tenant, it can be utilized by any user-defined tenants without the need for exporting.
Simplifies policy management across multiple tenants.
4. Example: Allowing Traffic Between VRFs
Traffic Requirements:
Traffic needs to be permitted between different VRFs.
Configuration Steps:
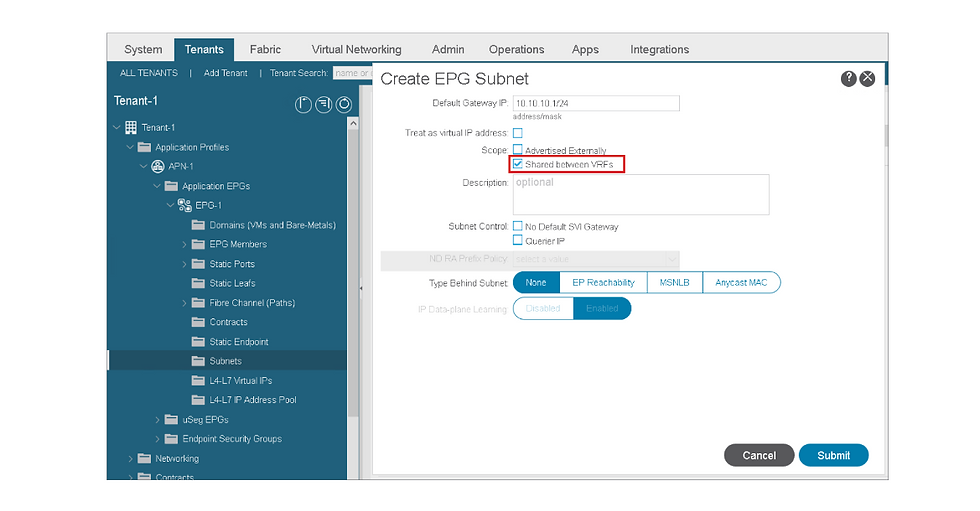
Bridge Domain (BD) Subnet:
Define a subnet within the BD that is shared between VRFs.
Provider Subnet Configuration:
Ensure that the shared subnet is configured on the provider side.
Consumer Subnet Configuration:
Similarly, configure the shared subnet on the consumer side.
Outcome:
By configuring the shared subnet on both the provider and consumer sides, traffic is allowed to flow between the specified VRFs.
Let's say EPG are in different tenants . Hence scope must be set to "Global".
Create a contract in Provider Tenant and it will be exported to consumer.
This contract will appear in consumer tenant under Imported contract
The imported contract is presented as consumed contract interface in the imported tenant.
Route Leaking Between L3Out EPG (External EPG) and Internal EPG
1. Shared L3Out Overview
Definition:
An L3Out configured with VRF route leaking is referred to as a Shared L3Out.
2. Scopes in Shared L3Out Subnets
Within the L3Out EPG, there are two distinct scopes:
Shared Route Control Subnet:
Purpose:
Designated subnet for route leaking.
Shared Security Import Subnet:
Purpose:
Informs other VRFs about the subnet-to-L3Out EPG mapping.
3. L3Out Subnet Configuration Requirements
Mandatory Configuration in Each L3Out EPG:
External Subnets for the External EPG Scope:
Purpose:
Declares which external routes belong to each L3Out EPG.
Consumer Side Requirements:
No Strict Requirements:
Unlike the provider side, the consumer side does not have stringent subnet configuration requirements.
Mapping Information:
Necessity:
Other VRFs must be aware of the subnet-to-L3Out EPG mapping to correctly apply contracts.
4. Differences Between L3Out and Internal EPGs
Internal EPGs:
Flexibility:
Do not require explicit subnet declarations for route leaking.
L3Out EPGs:
Mandatory Declarations:
Must define external subnets with the appropriate scope regardless of VRF route leaking.
5. Separation of Scopes for Granularity
Reason for Separate Scopes:
Granular Control:
Keeping Shared Route Control Subnet and Shared Security Import Subnet separate allows for more precise application of contracts.
Enhanced Security and Management:
Facilitates targeted policy enforcement and better management of route and security mappings.
6. Example: Allowing Traffic Between VRFs
Traffic Requirements:
Traffic needs to be permitted between different VRFs.
Configuration Steps:
Bridge Domain (BD) Subnet:
Define a subnet within the BD that is shared between VRFs.
Provider Subnet Configuration:
Configure the shared subnet on the provider side within the L3Out EPG.
Consumer Subnet Configuration:
Similarly, configure the shared subnet on the consumer side within the L3Out EPG.
Outcome:
By configuring the shared subnet on both the provider and consumer sides, traffic is allowed to flow between the specified VRFs.







Comments